Team accounts
MailSlurp supports team accounts for organizations. Team accounts allow you to create multiple users and share inboxes and email addresses and other resources between them. You can also enable SAML SSO for your team and use your existing identity provider (IdP) to manage user access.
Quick links
Portals
Organization overview
Organizations are a way to group users and resources together. Organizations can be used to share inboxes, email addresses, and other resources between users. Organizations enable SAML single-sign to MailSlurp via your own identity provider (IdP).
Name and slug
Each organization has a unique slug - this is an ID that is used in login links and API calls. You can use a more descriptive name for the organization name.
User access options
Users can access an organization by logging in via email one-time codes. You can also enable SAML SSO for your organization to use your existing identity provider (IdP) to manage user access. See the SAML setup section below for more information.
Email access links
Users wishing to access an organization via email access link can do so at https://app.mailslurp.com/organization/[YOUR_SLUG]. You can disable email access in the organization settings.
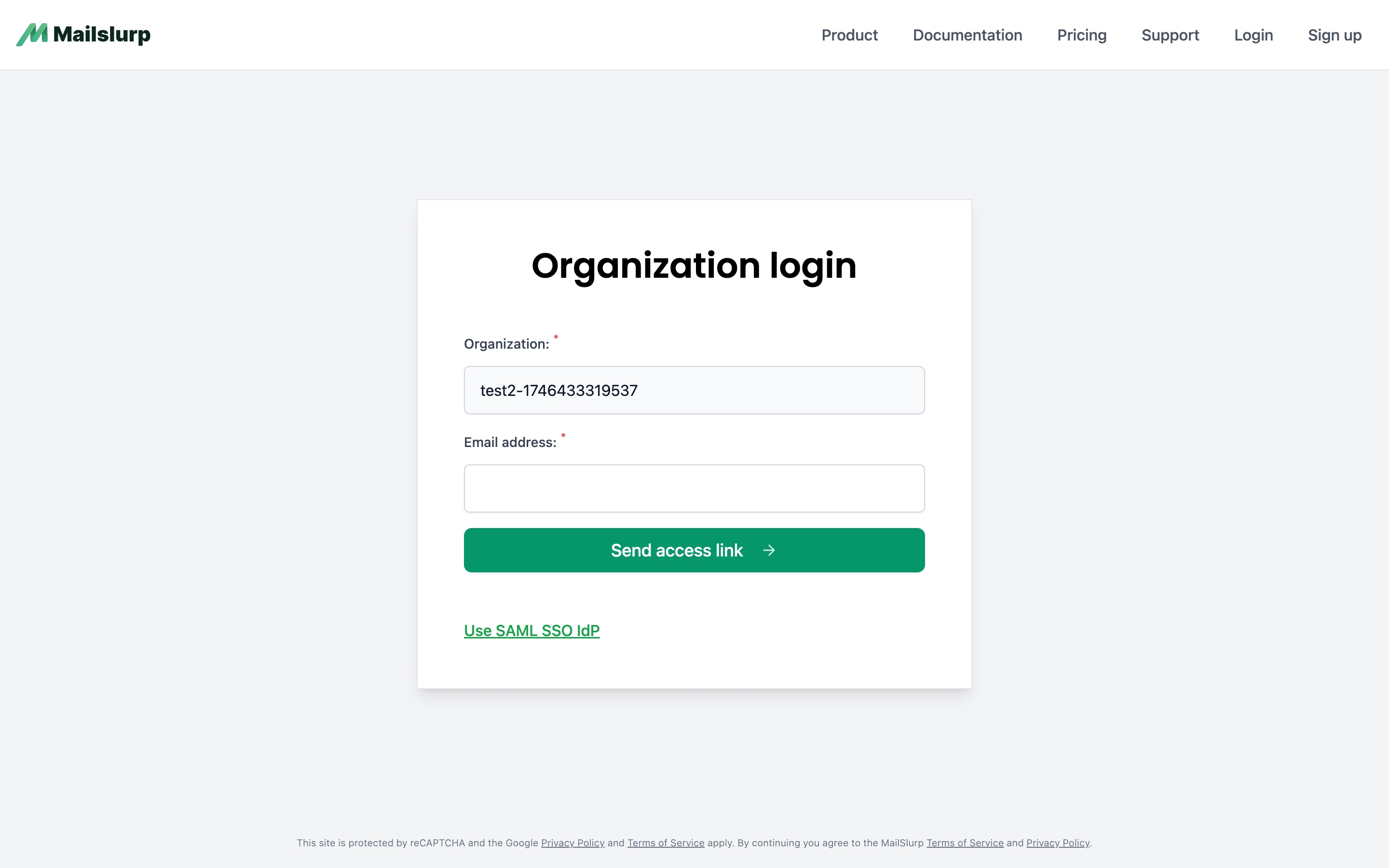
SAML SSO IdP
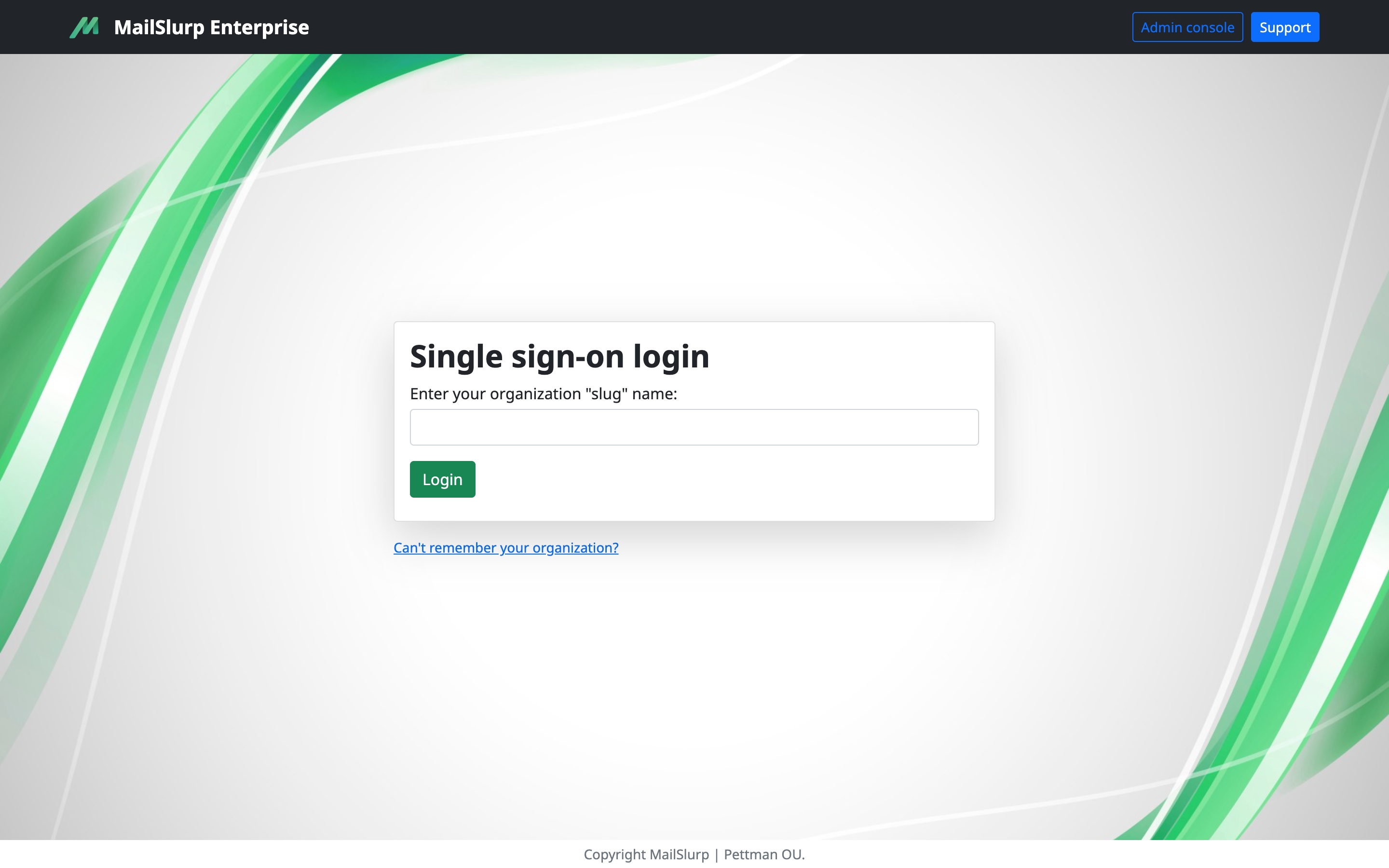
If you configure single sign-on (Okta, Azure AD, etc) for your organization then users will be redirected to your IdP to login. Once logged in they will be redirected back to MailSlurp with a valid session. You can initiate the login via your IdP or at https://enterprise.mailslurp.com/login?slug=[YOUR_SLUG].
Organization settings
You can configure organization settings to add custom branding and to disable user login via email link. This can be found on the organization overview page.
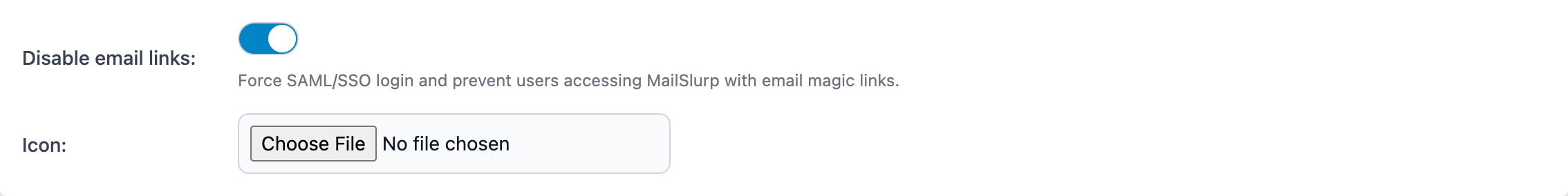
Logo and branding
You can configure a logo to be displayed on login screens and within the app using the organization settings page. A square icon with a background color is recommended.
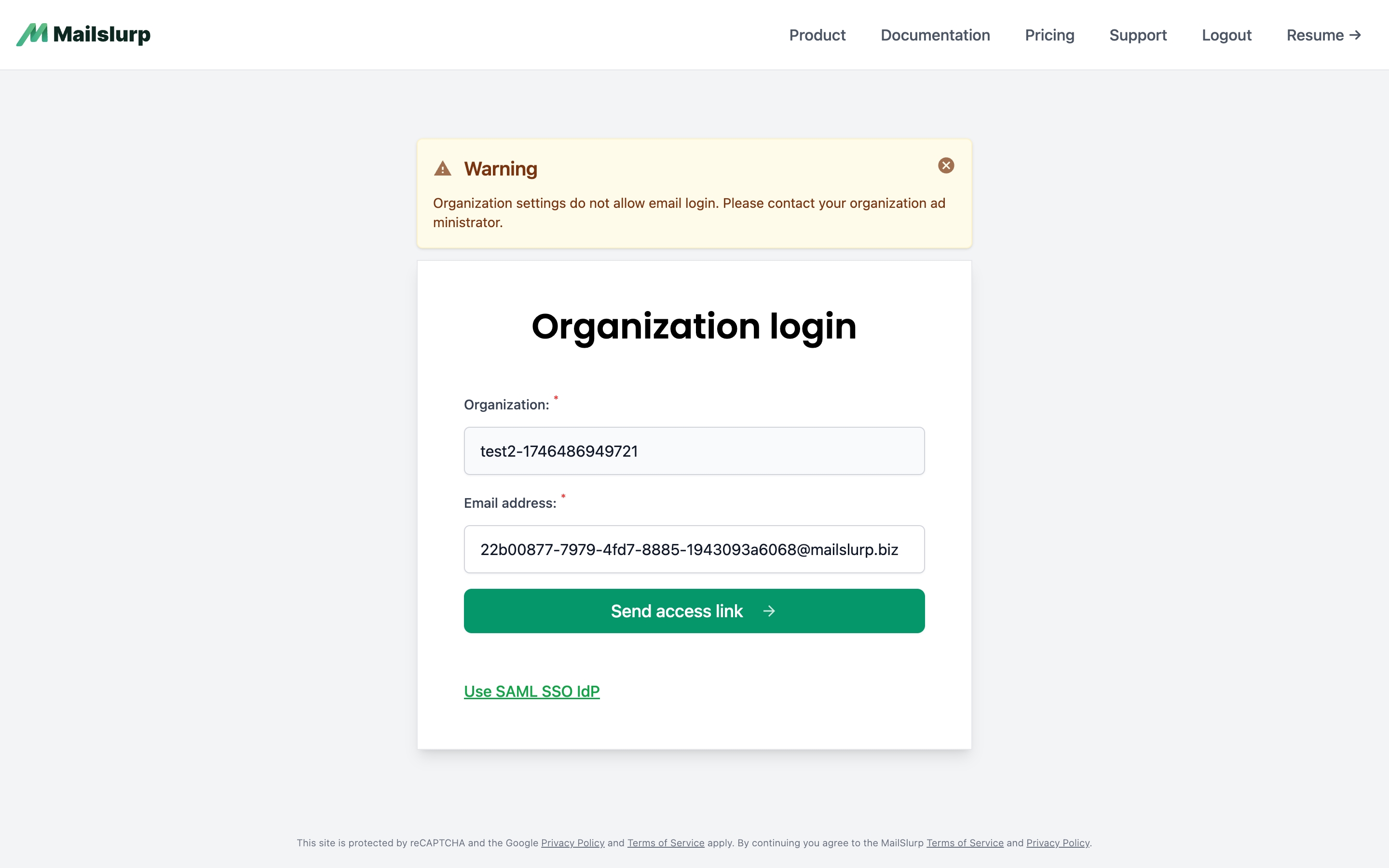
Disable email login
MailSlurp allows team members to login via their email and a verification code. This can be disabled in the organization settings to ensure only SAML SSO is used for login. Disabling email login with block users like so:
Managing organizations
You can manage organizations as the subscription holder account using the MailSlurp dashboard.
Create a team
To create an organization navigate to the organizations page in the dashboard. You can create a new organization or invite users to an existing team.
Adding additional seats
Subscription plans include a base number of user seats and additional seats can be added during upgrade on the subscription page.
Invite users
You can invite users to your organization
Managing users
You can add, edit, and remove users from your organization on the organization overview page in the dashboard.
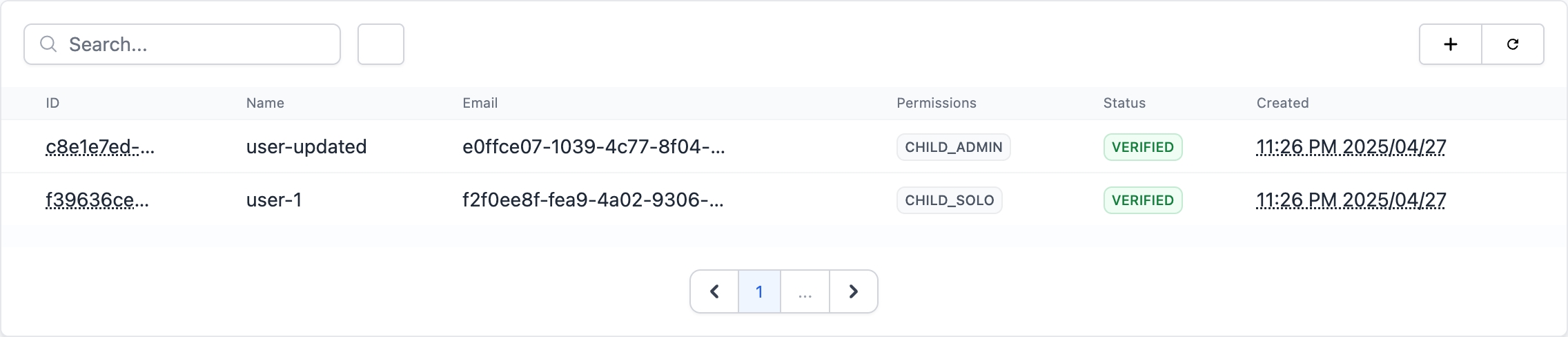
You can also change permissions and roles.
Setup SAML/SSO
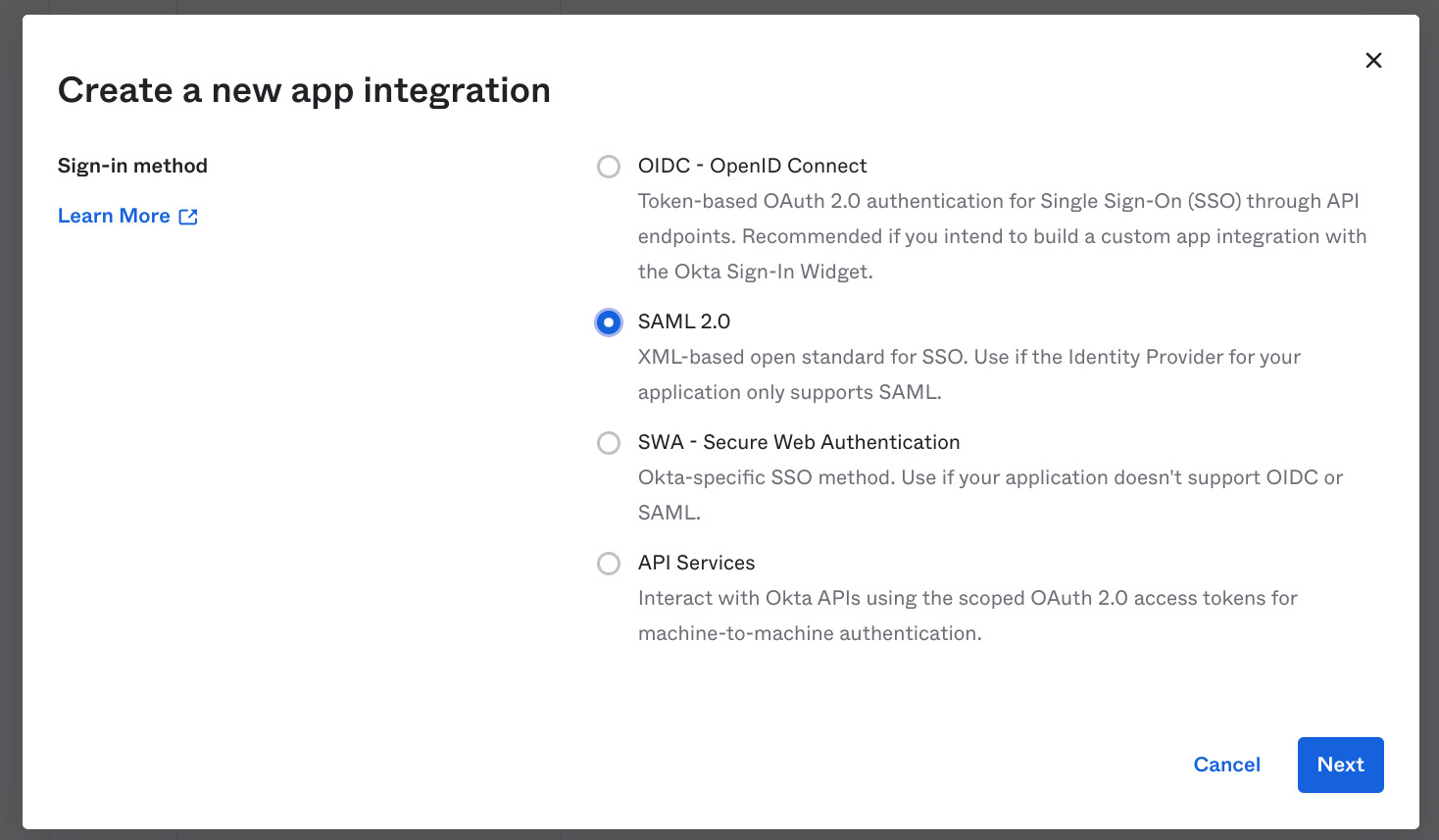
You can configure SSO SAML login via your IdP identity provider such as Azure, Okta, Active Directory or AWS Cognito. The process can be complicated so please contact support for assistance if needed.
1. Upgrade account for SSO
Ensure you have a plan that supports SAML sign-in or follow the upgrade guide if you don't.
2. Create an organization
Create an organization in the MailSlurp app.
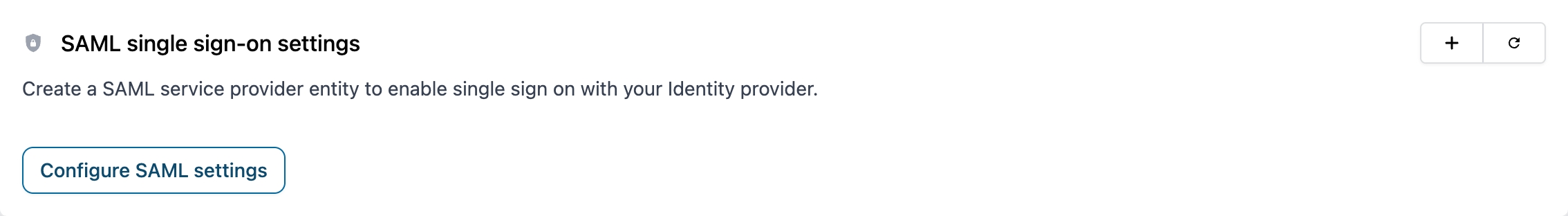
3. Configure SAML settings for the organization
Click the saml settings tab on the organization overview:
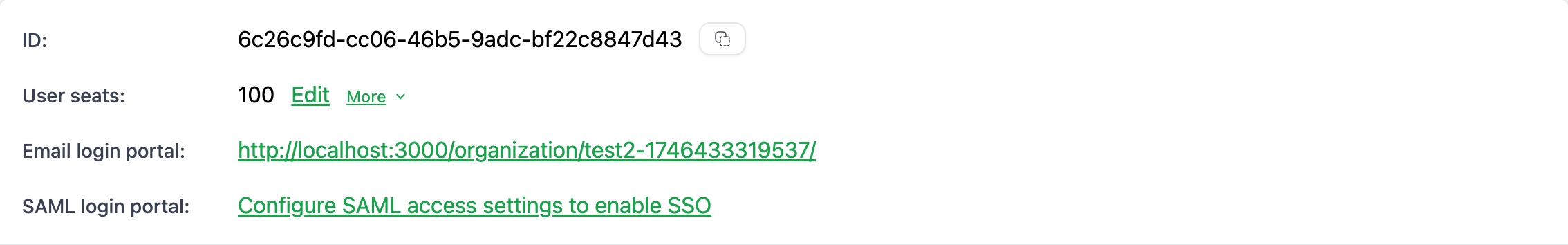
Or click the configure saml link in the access portal card:
4. Add the SAML service provider data to your IdP
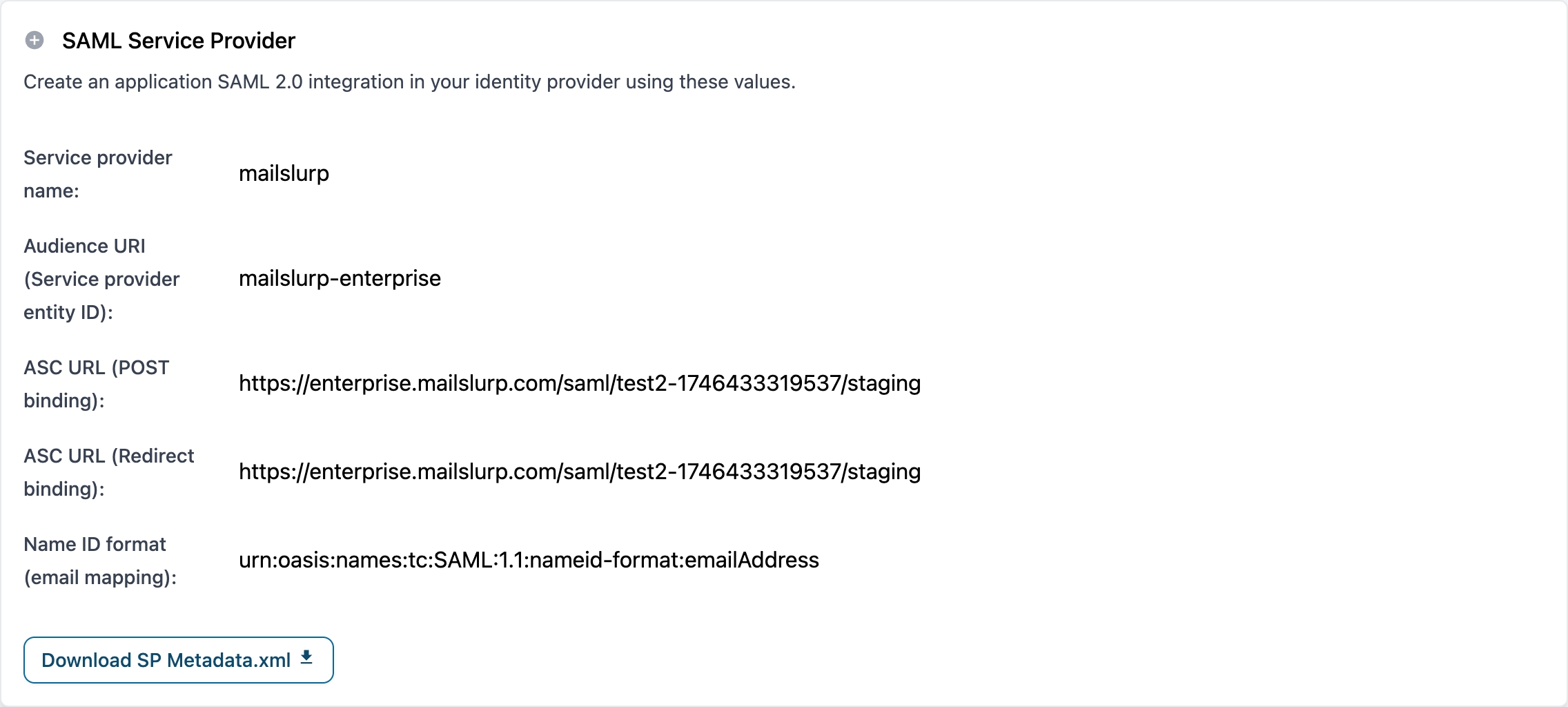
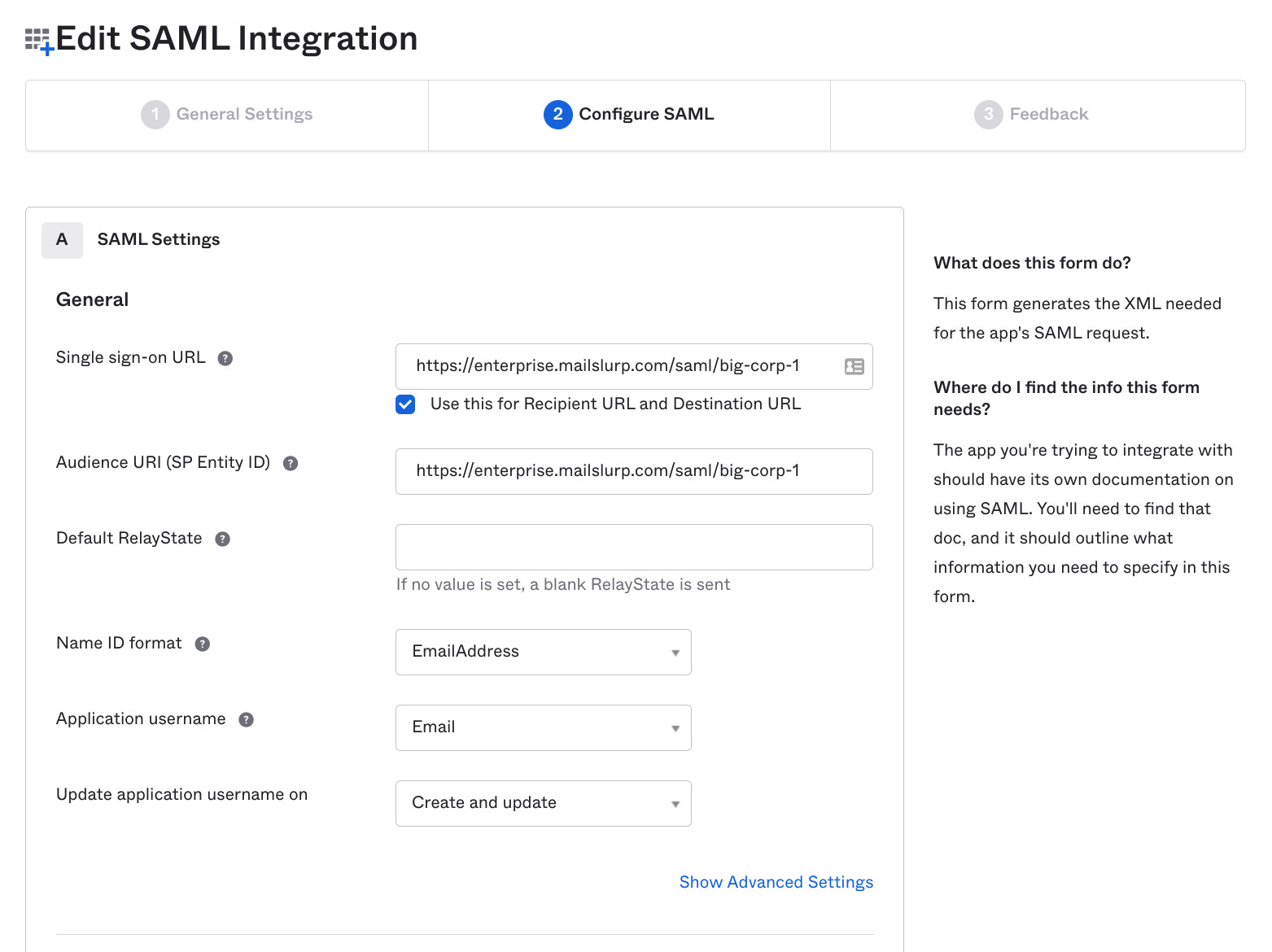
Next you need to create an application or service provider in your identity provider to is configured for MailSlurp's identity provider endpoints. You can copy the data shown in the service provider data card on the SAML settings page, or you can download the XML file and upload it to your IdP.
In Okta for example the service provider data is added like so:
Then the SAML settings can be added:
5. Obtain IdP SAML data and add to MailSlurp
Now you need to get the SAML configuration from your identity provider (Okta, AD etc) and add that to the SAML configuration in MailSlurp.
In Okta the SAML data can be found like so:
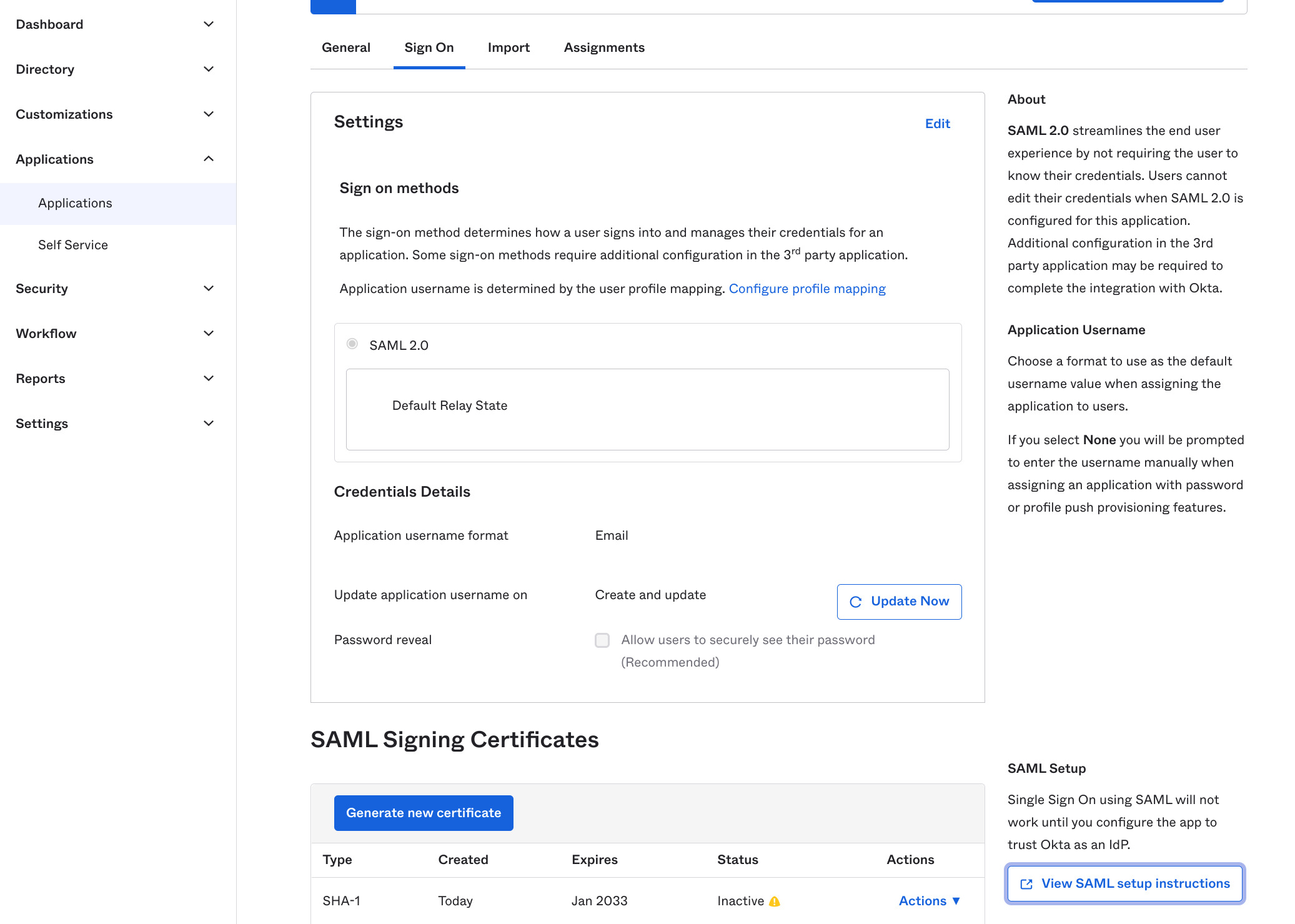
IdP settings typically look like this:
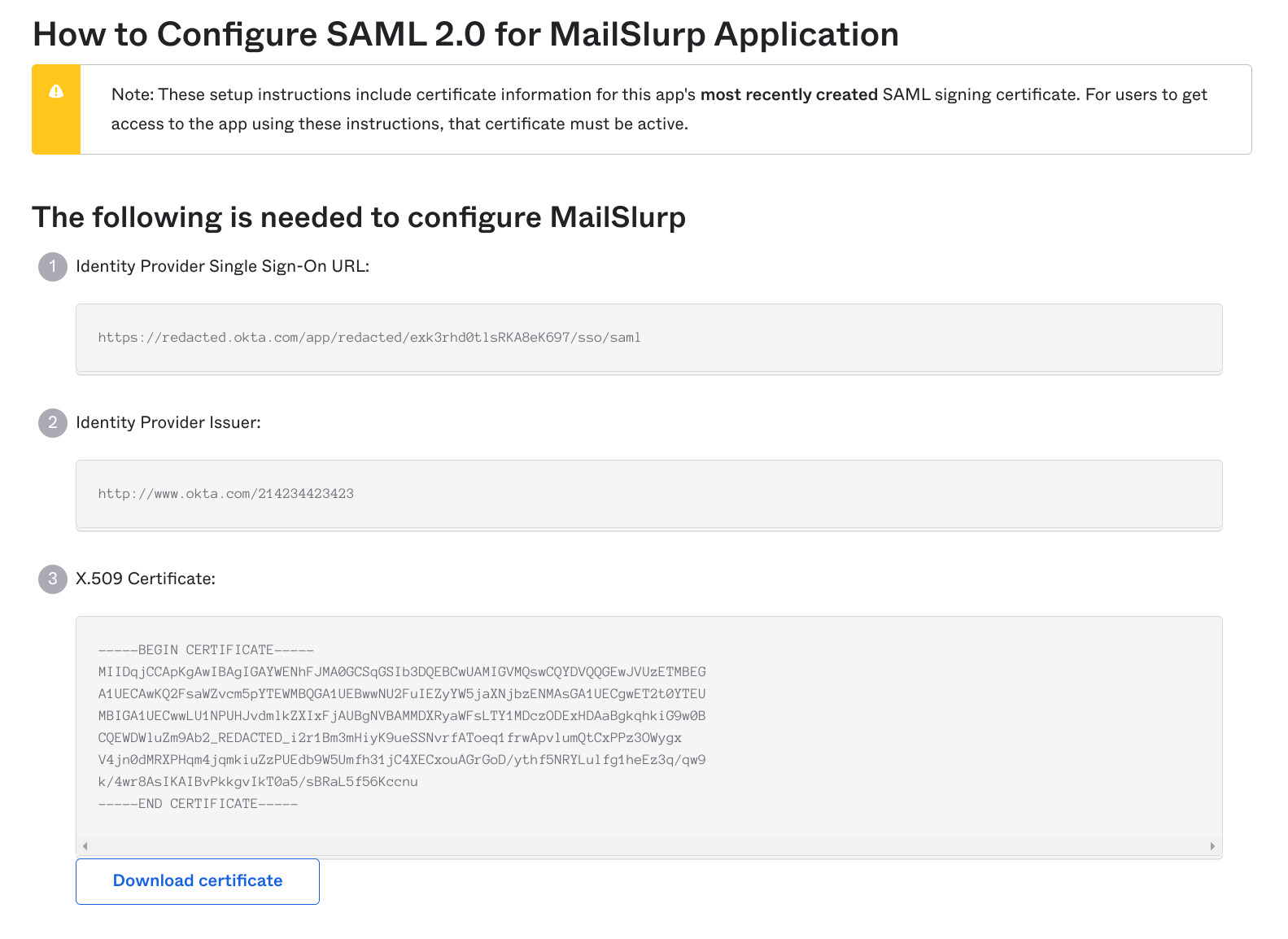
Take the data and add it to the MailSlurp SAML configuration. Here is a screenshot of the app with a test IdP configured:
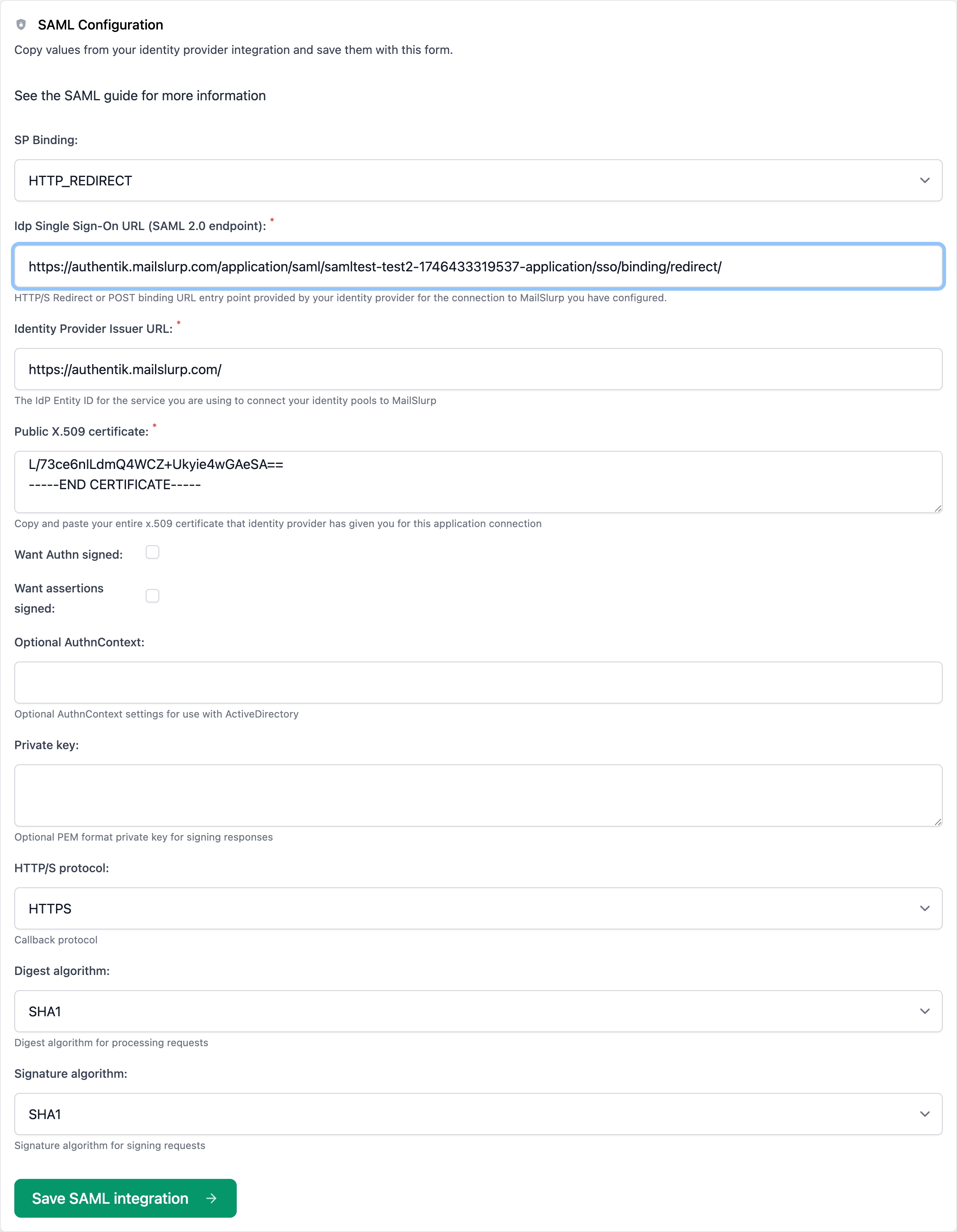
6. Double check entries
Make sure you enter exactly what your IdP tells you and configure AuthnContext and digest/signature algorithms as needed.
7. Save and test login
Once SAML is configured save the settings and view the organization. You will see a button to launch the SAML login screen. Click it to test your configuration.
![]()
SAML reference
Service provider meta data
Configure your application integration in your identity provider with these SAML endpoints. Be sure to add your own organization slug where indicated.
| Name | Value |
|---|---|
| Provider name | mailslurp |
| Name ID format | urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
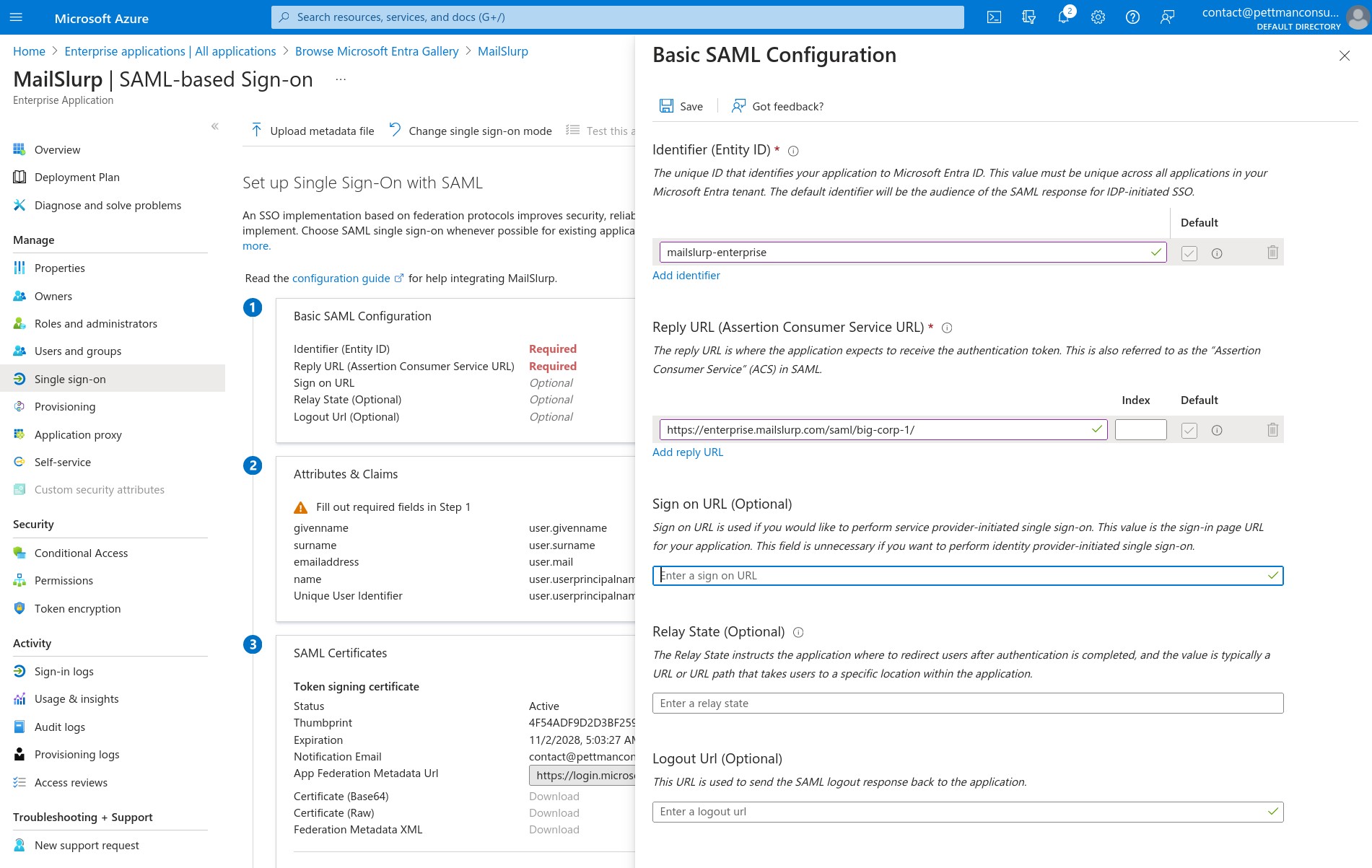
| Audience URI service provider entity ID | mailslurp-enterprise |
| Service provider metadata XML | https://enterprise.mailslurp.com/metadata?slug=[YOUR_SLUG] |
| Assertion consumer service endpoint ACS URL Redirect | https://enterprise.mailslurp.com/saml/[YOUR_SLUG]/ |
| Assertion consumer service endpoint ACS URL Post | https://enterprise.mailslurp.com/saml/[YOUR_SLUG]/ |
Okta SAML setup
- See the Okta guide
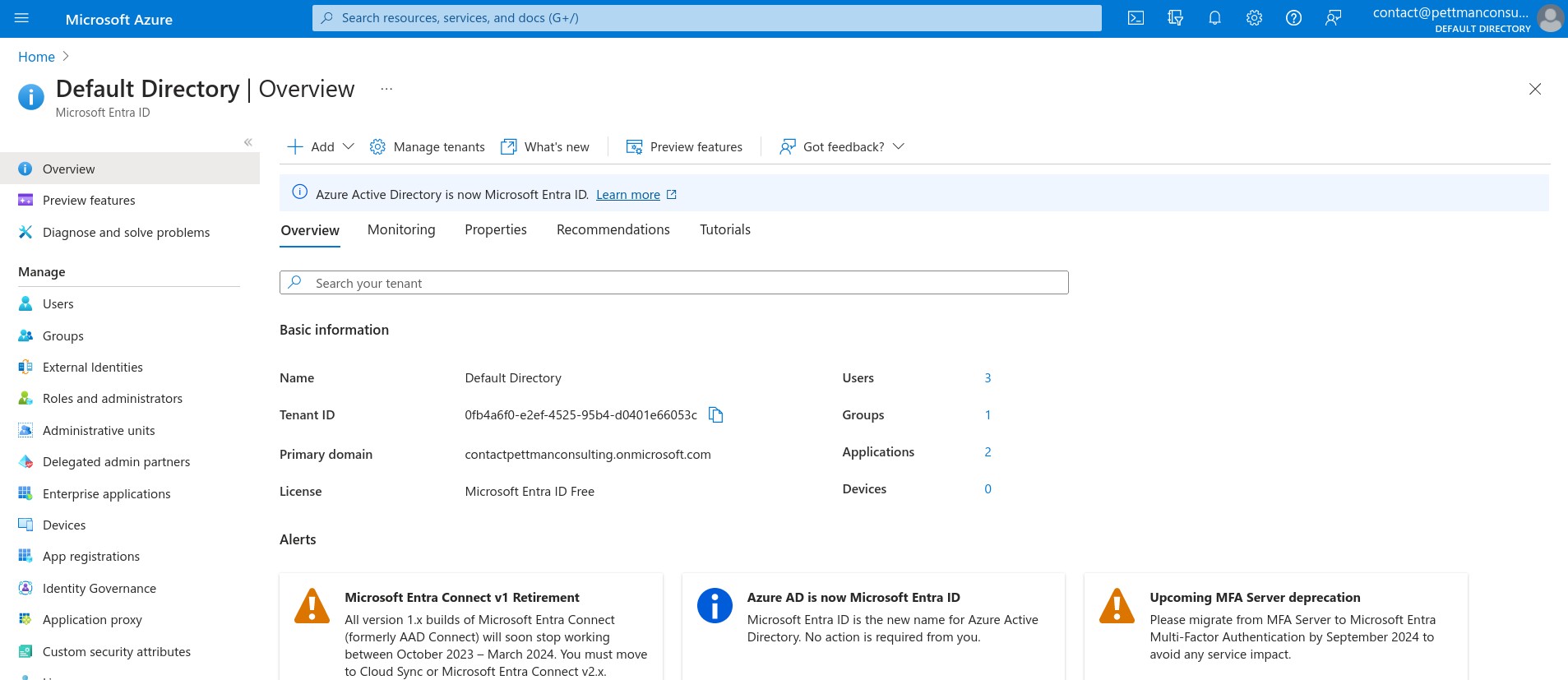
Azure AD / Entra ID settings
You can configure active directory via Azure AD / Entra ID enteprise applications. Go to Entra ID in the azure portal:
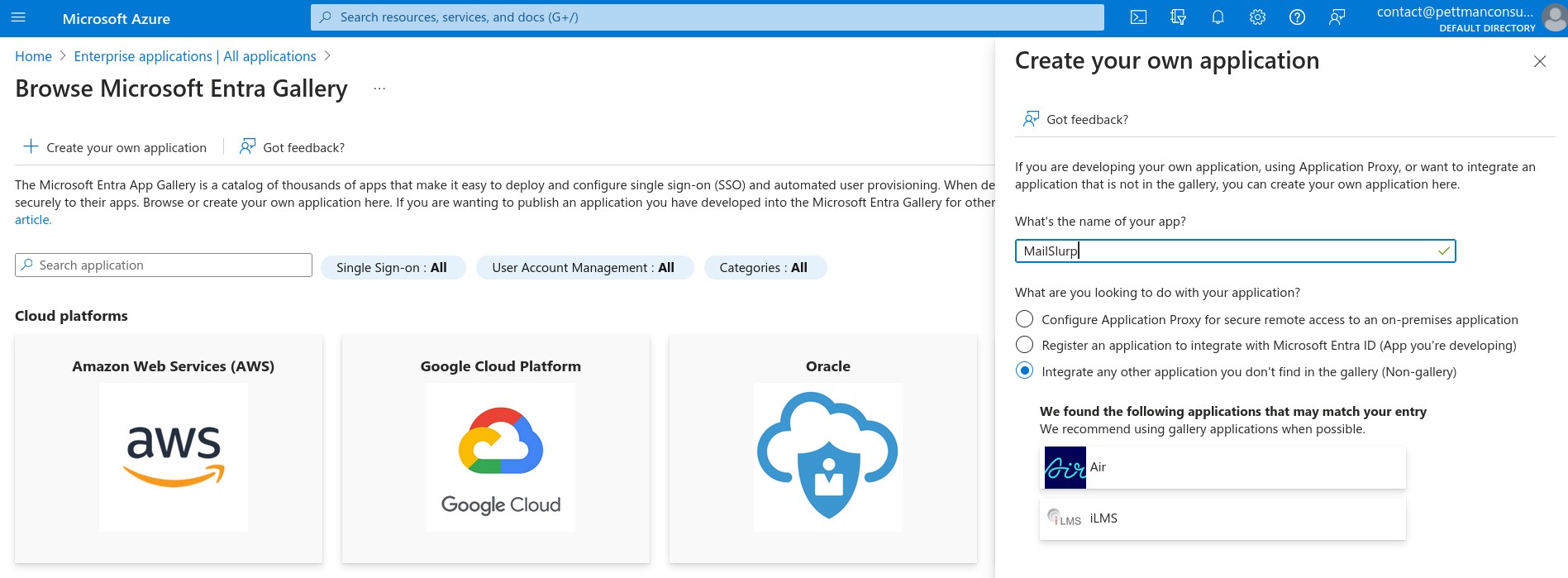
Then add a new application as a non-gallery application:
On the overview page click Set up single sign on:
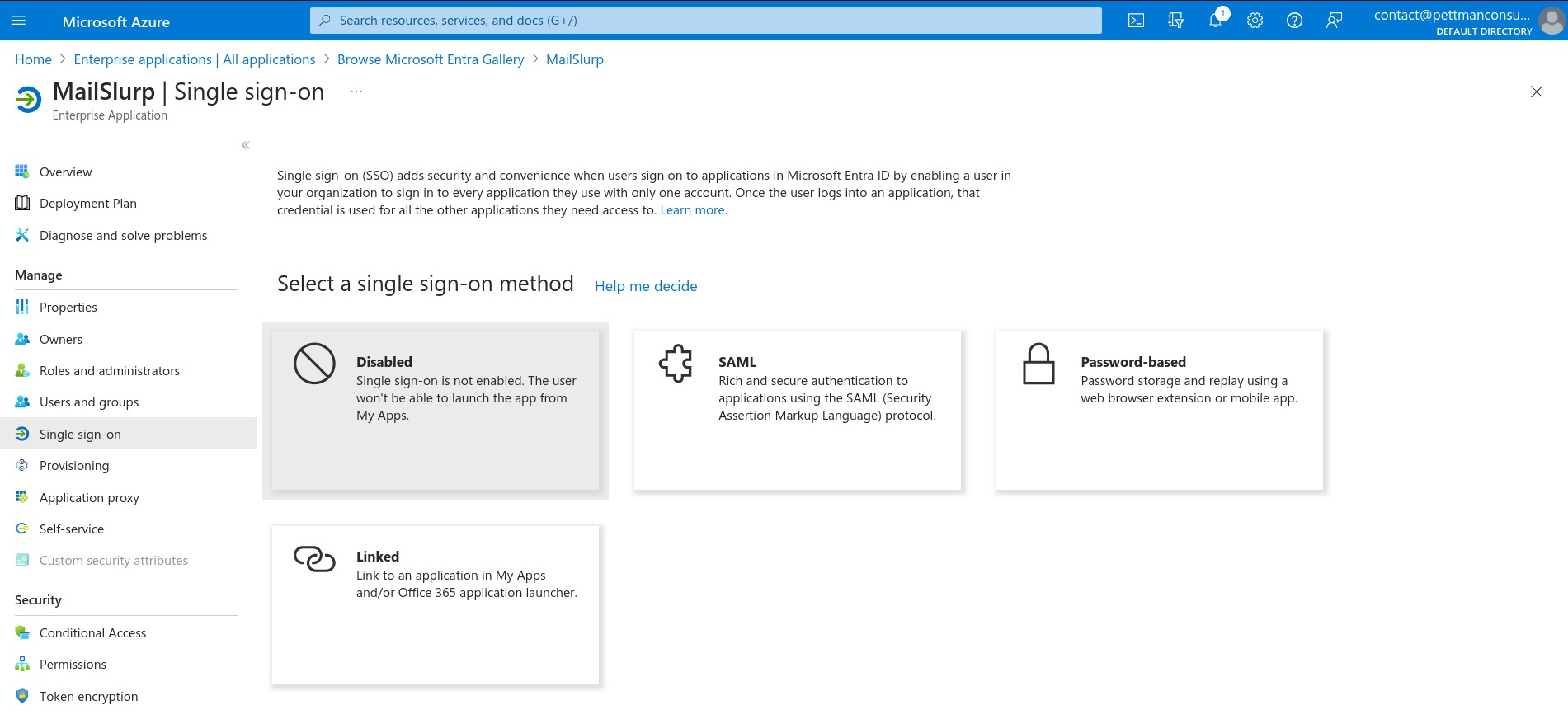
Then add SAML single sign on:
Then add the SAML SP data provider by MailSlurp:
Lastly, copy the IdP SAML data from Azure / Entra ID and add it to the MailSlurp SAML configuration.
** Tips: **
- SP Binding is
HTTP_POST - SAML 2.0 endpoint is
https://login.microsoftonline.com/<YOUR_TENANT_ID>/saml2 - Identity provider issuer URL:
https://sts.windows.net/<YOUR_ID>/ - Digest algorithm SHA256
- Signature algorithm SHA256
- Add a private key for signing
- Provision users in AD
- Launch the application from AD